Keeping your M365 safe 🔒 Simple yet effective ways for securing your Microsoft environment
What are some simple ways you can keep your Microsoft environment safe from attackers? Learn in this blog!

The inspiration for this post comes from the National Cyber Security Centre Finland, who have recently warned about breaches happening to M365 accounts and environments, with the amount of organizations breached going to up 121 during October 2025. Since I work with M365 Security every single day, I decided to write this article to list the simple yet effective things you should implement immediately, if not done yet.
How these attacks usually happen
You might have already guessed where the attack starts. It's of course our old friend phishing. In the latest attacks, it has been in the form of an "invoice.pdf" file that "was shared to you", leading the victim to a fake Microsoft login page. As a cybersecurity professional, you think people wouldn't fall for these anymore, but the truth is that they still work. I've recently seen even Microsoft MVP's get their accounts taken over, so no one is immune!
After initial access, the attackers go through the users' Outlook and their emails, contacts and other information they can gather of the company getting attacked. After this, they send further phishing emails to every contact the victim has in their Outlook, trying to compromise more accounts.
How do you stop these attacks from happening?
The methods which you can use to easily shield your organization from these kind of attacks are the ones you'd usually expect!
Multi-factor Authentication - NO EXCEPTIONS
This one is as simple as it sounds. Every single user should have MFA enabled, and there should be zero exceptions to this rule (even your break glass -accounts should have MFA, for example a FIDO key). Microsoft says that MFA prevents 99,9% of identity-based attacks, which makes it even more weird that some companies still don't enforce it strictly enough.
Normal users should be using their cellphone with the Authenticator App, where admins should be prompted for phishing-resistant MFA when accessing admin portals. I would recommend FIDO keys or Windows Hello for Business for this.
The only situations where I see users complaining about MFA is when it's done wrong. Don't make users re-do MFA every hour, and make sure your applications support SSO. In your normal day-to-day work on your work laptop, you shouldn't be required to punch in your MFA code even once.
Conditional Access
Conditional access policies are one of your primary lines of defense against these attacks, but it's also the part where many make it much more difficult than it should be. Here are the basic principles and policies you should have:
- Require trusted company devices for all logins
- Require for all apps, most important apps, or if you can't require them, make sure the user has to MFA every single time
- Block all legacy authentication
- SMTP, Exchange ActiveSync and other protocols should be blocked outright since they don't support modern MFA. You can whitelist specific accounts if legacy applications require them.
- Block untrusted countries
- You cannot block attacks outright by only allowing your operating countries, but it doesn't hurt to block some countries (for example one specific neighbor country of Finland)
- Risk-based controls
- If you have E5 or Entra ID P2, utilize Identity Protection, and block logins if User Risk or Sign-In Risk are "High". The deduction system that determines the risk level is surprisingly good and really helps stopping attacks that otherwise would get through.
Token Protection
If you have been working around Microsoft security in the past few years, you have no doubt heard of AITM or "Attacker in the Middle" -attacks. These attacks manage to bypass MFA by stealing a session token rather than a password.
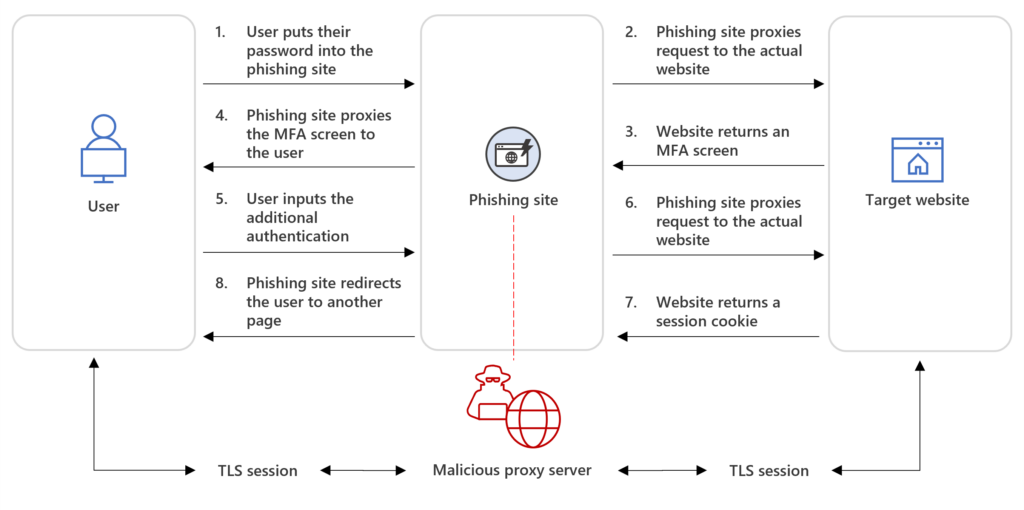
Microsoft has recently tackled these attacks with various features you can look to implement, with one being Token Protection. This feature works by binding your session token to the device it's created for (for example, your work laptop) and automatically invalidates that token if someone tries to use it with another device.
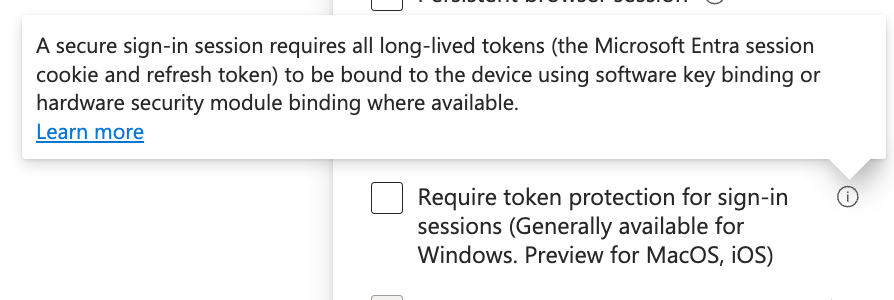
Token Protection is now Generally Available for Windows and in Preview for MacOS. It currently also doesn't support every client, but the list of supported ones is getting better all the time. You should definitely check this feature out and maybe enforce it especially for admin actions.
Training
This is along with MFA the one thing people might start to be tired of hearing. However, training your workforce tackles the root cause of these account breaches: falling for a phishing attack.
As a security analyst I have seen a variety of phishing emails - and they have gotten really good. I don't blame less tech-savvy people for falling for these attacks. But what you should do as an admin is start training your people to notice these attacks and report them to the admins - because then you can block and mitigate the attack faster.
Microsoft has a tool for this in the E5 Security -Suite: Attack Simulation Training which is included in Defender for Office. This feature lets you create phishing campaigns with templates or totally custom messages, and then follow the results on what your employees decide to do with them - do they input their login credentials, report the mail to admins or delete the email outright. Attack Simulation Training has been improving over the years and I know many companies pay for a 3rd party service doing the same thing, so you could even save some money by implementing this feature!
What should you do as an admin if you think you have been attacked?
I'll try to keep this as simple as possible so you don't have to be a seasoned cybersecurity professional to understand it. There are a couple of things which are important to combatting these attacks:
- Visibility
First, you have to see when an attack is happening. Relying on end-user information is not good enough. This means that you have to implement Sentinel to store your logs and alerts to be raised when something suspicious happens. This means that you don't have to stare at the logs 24/7, but can react when something happens.
- Automate
Another thing you can do with Sentinel and Defender XDR is automate response. In addition to Microsoft's own Attack Disruption for AiTM, you can create custom automations that reset users sessions, disable their account or require a password reset in a case where it seems the account might have been breached.
- Recover and mitigate
If you didn't manage to stop the attack before it happened, your next best thing is to recover and mitigate the threat as well as possible. This means checking the next things:
- Go through logs and formulate an attack timeline and report: What happened? When did it happen? Where did it come from? What did the attacker do? When did you notice it? When did you stop it?
- If you haven't already done it, reset the victims password and invalidate all sessions. This boots the attacker out if they have a valid session.
- Check the victims MFA methods and make sure the attacker didn't register their own device as a valid MFA method. This is sometimes done to establish persistance.
- Write an in-depth report on the root cause of the attack, how you mitigated it and what you should do to be more resistant to these attacks in the future.
The last one is not only important for your own company and your technical development, but also important as a document you can give to partners and clients who might have been affected by your breach. This can happen if the attacker for example sends phishing mails to all of the victims contacts.
What next?
You can spend hours and hours perfecting your conditional access policies or training your people for the 12th time in a month, but you have to realize some things:
- Attackers will innovate, so you can't stop developing your defenses
- Sometimes, you cannot stop an attack, even if you do everything right. The next best thing you can do is to reduce the blast radius.
And the most important one I'll leave you with: Don't let perfect be the enemy of good. Don't spend time trying to craft a 110% perfect solution, rather implement the solution that gets you 99% there. Because any kind of security is better than no security. Just like with MFA stopping 99% of identity attacks, sometimes the most effective solution doesn't have to be the coolest and most appealing one.
